WordPress has a simple login page that allows webmasters to make alterations of all kinds, with a fairly secure permissions management system and thousands of plugins that help increase their functionality.
The problem is that this login page is the target of hackers trying to enter the private section at all times, and we must protect it to the maximum to avoid both an invasion and an excessive amount of access to the database. Although the web is password protected, if someone tries to perform a brute force attack, thousands of combinations will be tested in a short time, saturating the server, which will have to verify all of them in the database, consuming resources.
Here are three things that must always be done to protect that:
1- Protect the wp-admin directory:
To do this, simply create a .htpasswd file and put it in a directory inside the server. The content of this file is an extra encrypted login and password, which you can do with pages like this one.
Once the file is created, it is necessary to create an .htaccess in the wp-admin directory and add the following lines:
[gdlr_code title=”htaccess” active=”no”]
AuthName “text”
AuthType Basic
AuthUserFile “/home/username/example.com/.htpasswd” (with path where htpasswd has been saved)
Require valid-user
[/gdlr_code]
2 – Protect the wp-login.php file:
The entry to WordPress can also be done by the wp-login file, so it must be protected from the .htaccess file of the website using:
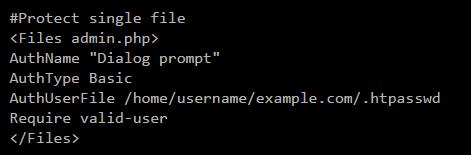
Although in this case it will be necessary to specify wp-login.php inside the code.
3 – Block access from the WordPress mobile app:
Although directories and files are protected, hackers may attempt to log in using the WordPress mobile app, as that app does not use traditional pages. In this case it will be necessary to block the access to the file xmlrpc.php from the .htaccess, responsible for the update and identification from third-party platforms. The lines of code are simple, also in the main .htaccess of the website:
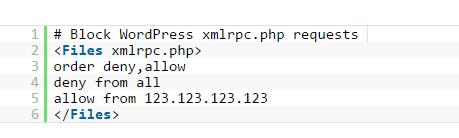
In this case the access to IP 123.123.123.123 has been released, so that only those who have such IP can perform the updates from the desired application.
Three simple steps that will allow more security without installing any plugins.










No Comments
Leave a comment Cancel