What is Sathurbot?
Again, cyber criminals know how to play their cards. On this occasion, they have used WordPress websites to distribute a backdoor between users. Sathurbot is the name of the threat and has already infected a total of 20,000 users. They use ads that promise to download series and movies for free.
However, the end result is that the user will unload the back door. The company ESET has been in charge of carrying out an analysis of the behavior of the threat. They have determined that it is being distributed since June of last year, although the level of activity for the moment has been quite low.
From the security company confirm that cyber criminals are using management accounts of websites to modify the configuration of the portal and thus publish the threat at hand. They indicate that the attacks that are being carried out are based on brute force, using dictionaries with the most common passwords, resulting in another additional problem that we will detail later.
Offering fake content to spread the threat
As we have already indicated in the beginning, the attackers offer content that indicates the possibility of downloading both movies and series episodes completely free of charge. However, this is not so, and what the user is actually downloading is the threat. It is designed to affect users with Windows operating system and suspicions should appear right at the time of download, when it only lasts only a few seconds. In the case of being a film or series the time invested should be much higher. However, taking into account that the download is a priority of a torrent, the user falls into deception with ease.
It is true that at the moment the infection rate is quite low and that the activity of the presence of the threat on the Internet has not been remarkable.
After the download, what happens?
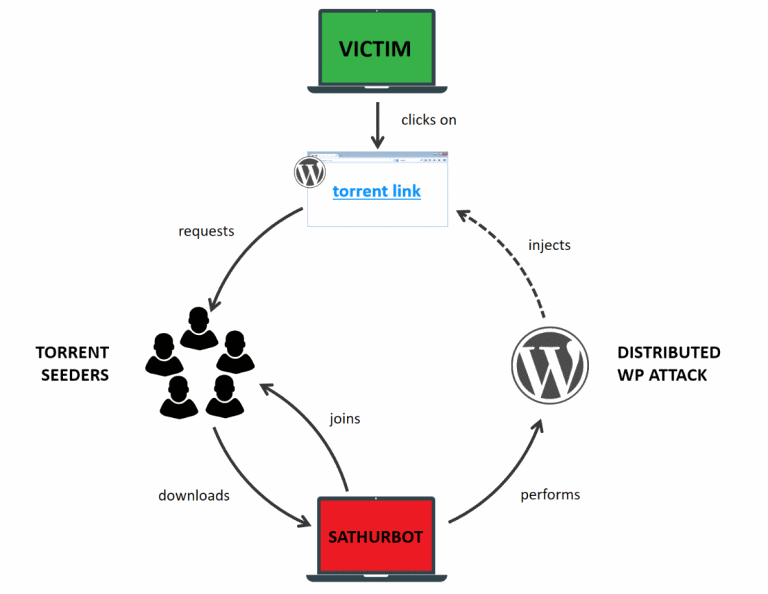
After executing the file, the first thing the user receives is a warning that an error has occurred and the installation can not be started. The problem is what the user does not see. While you are paying attention to this message, all the components that the threat needs to function correctly are being installed in the background.
From ESET have detected the presence of a module that is responsible for communication with the remote control server. Sathurbot has the ability to update itself automatically.
Although it is WordPress that brings together a high percentage, it must be said that others such as Drupal, Joomla, PHP-NUKE, phpFox or DedeCMS have also been affected, although for the moment to a lesser extent.
The passwords obtained are used to attack other services
Since cyber criminals are finding in the account management settings e-mail addresses, cyber criminals have also opted to try out fortune on these services. Although not highly recommended, users reuse passwords in different services. This practice implies that if one is affected it is very likely that the rest will also.












No Comments
Leave a comment Cancel